The computerization of most processes has led companies to dependence on their asset of computer data and the systems that manage them and bad information management is no longer a viable option.
Systems and organization are by their nature vulnerable and there are many threats (human and otherwise), coming from both outside and inside the company perimeter. The established functions therefore recognize information risk management as of vital strategic importance and a key component of the overall business strategy. Information risk management is important for all entities regardless of size or structure: people within organizations must be encouraged to manage the associated risks and to consider such management as an integral part of their daily operations.
Without appreciation of the role they play, each employee can undertake activities or on the contrary not undertake any, thus leaving the organization exposed to unnecessary risks. In fact, many companies still struggle to understand how to measure and quantify the impact that the quality of information has on their performance.
Information Risk Management (IRM) is a process for identifying, controlling and eliminating or minimizing uncertain events that can damage the resources of an IT system, and is one of the fundamental aspects of Corporate Governance.
The main objectives of the IRM first of all include confidentiality in order to ensure that information can only be used by people who are identified and authorized to use it. Then there is the aspect inherent to the integrity, or to the protection of the data itself from any unauthorized changes or cancellations. Last but not least, the objective of information risk management is that data and information are available, but only when necessary.
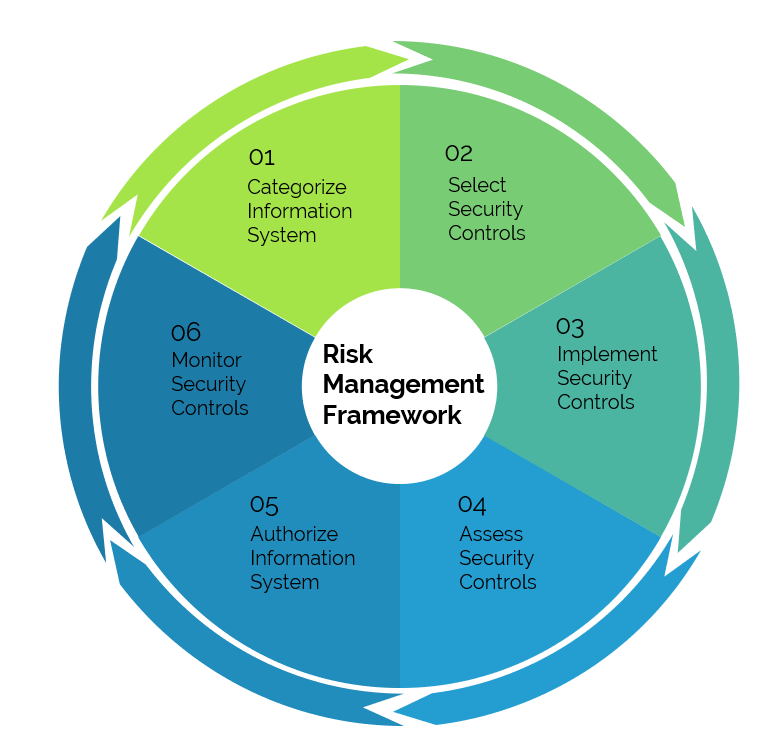
The main activities addressed within the IRM are the following:
• Information Security & Management: management of information security at all levels, such as, for example, the definition of a correct organizational structure with roles / responsibilities for the management of information security.
• Security, Risk Assessment & Management: identification of the risks and management of the same through the main reference standards and verification of the maturity of the models adopted.
• Logical access management: management of access to information commensurate with users’ duties and the risks deriving from unauthorized access to information.
• Business Continuity Management: management of risks deriving from the unavailability of information systems following disastrous events such as interruptions or outages.
• IT Internal Audit: verification of the control systems implemented by the companies and consequent carrying out of corrective actions.
• Cyber Security: prevention of any threats to information security both externally (hackers) and internally (unfair employees).
The function of risk management (RM), therefore, is to supervise and protect the value of an organization. By preparing a methodological framework that allows the full operation of each company area, through a coherent and controlled performance of each activity, risk management guarantees not only a comprehensive and structured understanding of the company with the related construction and planning of priorities, but also the protection of its information assets, know-how and Brand Reputation. The adoption of this set of technologies allows, among many applications, to monitor the use or management of personal information within company processes and to comply with current regulations in terms of Privacy and GDPR.

Recent Comments